Cybersecurity
Defend, detect, and secure: We are your shield in the digital realm
Keeping your applications and networks secure
In an era of constant digital evolution, our cybersecurity services offer a robust defense-in-depth approach to protect your organization’s applications, networks, and data from an array of cyber threats. Beyond safeguarding information assets, we add value by assisting clients in compliance with regulatory requirements and navigating the risks inherent in today’s dynamic digital landscape.

One size fits none – Our custom cybersecurity solutions
Regardless of your organization’s size or industry, we have the experience and expertise to tailor a security solution that meets your unique needs.

Security Assessments
Our team is highly specialized and experienced in providing end-to-end cybersecurity solutions. We take a holistic approach to security, starting with a comprehensive assessment of your organization’s current security posture. Our digital security assessments cover a wide spectrum of planning strategies and methodologies.
Key Services
- Gap assessments and penetration testing
- Dark web monitoring
- Network security and design reviews
- Digital forensics and incident response planning
Managed Security Center
We are a reliable managed services provider specializing in network security. Our 24/7/365 monitoring ensures your organization’s assets are always protected, giving you the peace of mind that comes with knowing your network security is in capable hands.
Key Services
- 24/7 managed SOC
- Vulnerability monitoring & management (IT/OT)
- Threat hunting
- Incident response & triage
- Advisory services and devices health test monitoring

Governance and Compliance.
We offer advisory and consulting services for navigating digital regulations. We help develop a comprehensive governance and compliance strategy tailored to meet legal and regulatory requirements, providing the necessary tools and resources for ongoing compliance.
Key Services
- NIST cybersecurity framework
- ISO 27001 auditing & compliance
- GDPR/HIPAA/PCI-DSS compliance
- Policy development & implementation
- Identity & Access Management (IAM)
- Disaster recovery planning
Elevating Cybersecurity Management: The RTCS Methodology
The RTCS cybersecurity methodology is a proactive approach that identifies an organization’s unique risks and vulnerabilities. We collaborate to develop a comprehensive security strategy focused on detection, validation, reporting, and response. CISOs face challenges in creating a robust cybersecurity program due to budget constraints, lack of expertise, and evolving threats. Managed security services offer a solution by supplementing internal teams with the necessary expertise and resources.
 Detection
DetectionThis step involves deploying advanced security technologies and processes to identify potential threats and vulnerabilities. It includes continuous network monitoring for signs of intrusion or malicious activity, along with regular vulnerability scans and penetration testing. |
 Validation
ValidationUpon detecting a potential threat or vulnerability, it must be validated to ensure its authenticity. This process involves verifying the source and intent of the threat, as well as assessing its potential impact on your organization. This validation enables quick and decisive action to be taken. |
 Reporting
ReportingOnce a threat or vulnerability has been validated, it is crucial to report the findings to the appropriate parties. This includes internal stakeholders, such as your incident response team, and external agencies, such as law enforcement or the relevant regulatory bodies. |
 Response
ResponseThe last step in our methodology is to develop and implement an effective response plan tailored to specific threats or vulnerabilities and consider their potential impact on your organization. Having a well-defined response plan in place is crucial for quickly resolving incidents. |
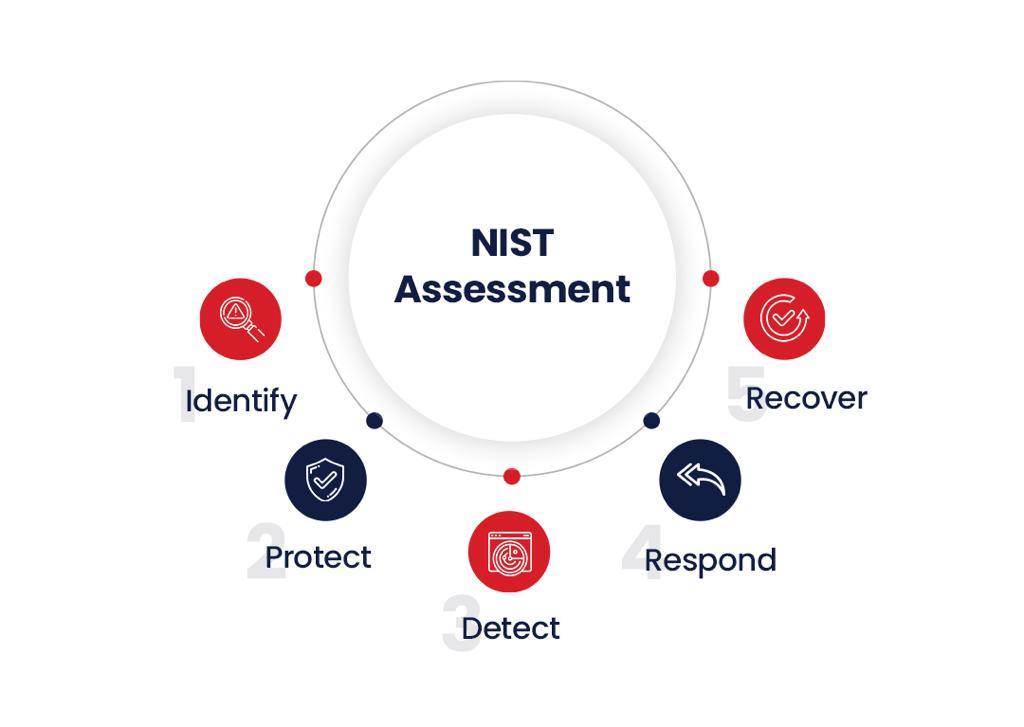
NIST framework and RTCS in cybersecurity synergy
Harmonizing seamlessly with the NIST framework, RTCS enhances the development of a resilient cybersecurity strategy. RTCS, with its focus on adaptability, complements NIST’s structured risk management. This integration empowers organizations to proactively identify, protect, detect, respond to, and recover from evolving cyber threats. The result is a dynamic strategy that ensures both security and adaptability in the face of ever-changing risks.
Our enterprise-class cooperation models
Handle project-based or ad-hoc needs with our customizable cybersecurity services. From implementing new security solutions to conducting assessments, we offer peace of mind for your business. Whether it’s a specific project or an annual security assessment, we’ve got you covered within your budget.
Managed cybersecurity services
By outsourcing the cybersecurity management of your security program to RTCS, you can focus on running your business while we take care of all of your security needs.
RTCS has established a culture of strong privacy guidelines and leading security measures. When working with our team of experts, you can be confident that your applications and network are safe and secure. With 24/7 monitoring and response, you can rest assured that your business is always protected during and outside of your standard business hours.


Managed IT services
Beyond cybersecurity, RTCS offers a full suite of managed IT services for efficient business operations. Our services, including cloud optimization, data center management, multi-zone NOC, end-user management, and outsourcing, are tailored to meet your specific needs. Whether you require consultative services or IT infrastructure management, we have the right solution for you.
Achieving robust cybersecurity goes beyond internal team resources
Cybersecurity is pivotal for businesses, often left to internal teams. However, establishing a robust posture exceeds internal capacities. CISOs grapple with crafting comprehensive programs amid budget constraints and evolving threats, all while keeping the business operational. Investing in managed security services becomes crucial, empowering businesses to navigate challenges, with the needed expertise and resources. RTCS offers cutting-edge cybersecurity services aimed at assisting your organization in developing cyber resilience from within.
 We're Hiring
We're Hiring



